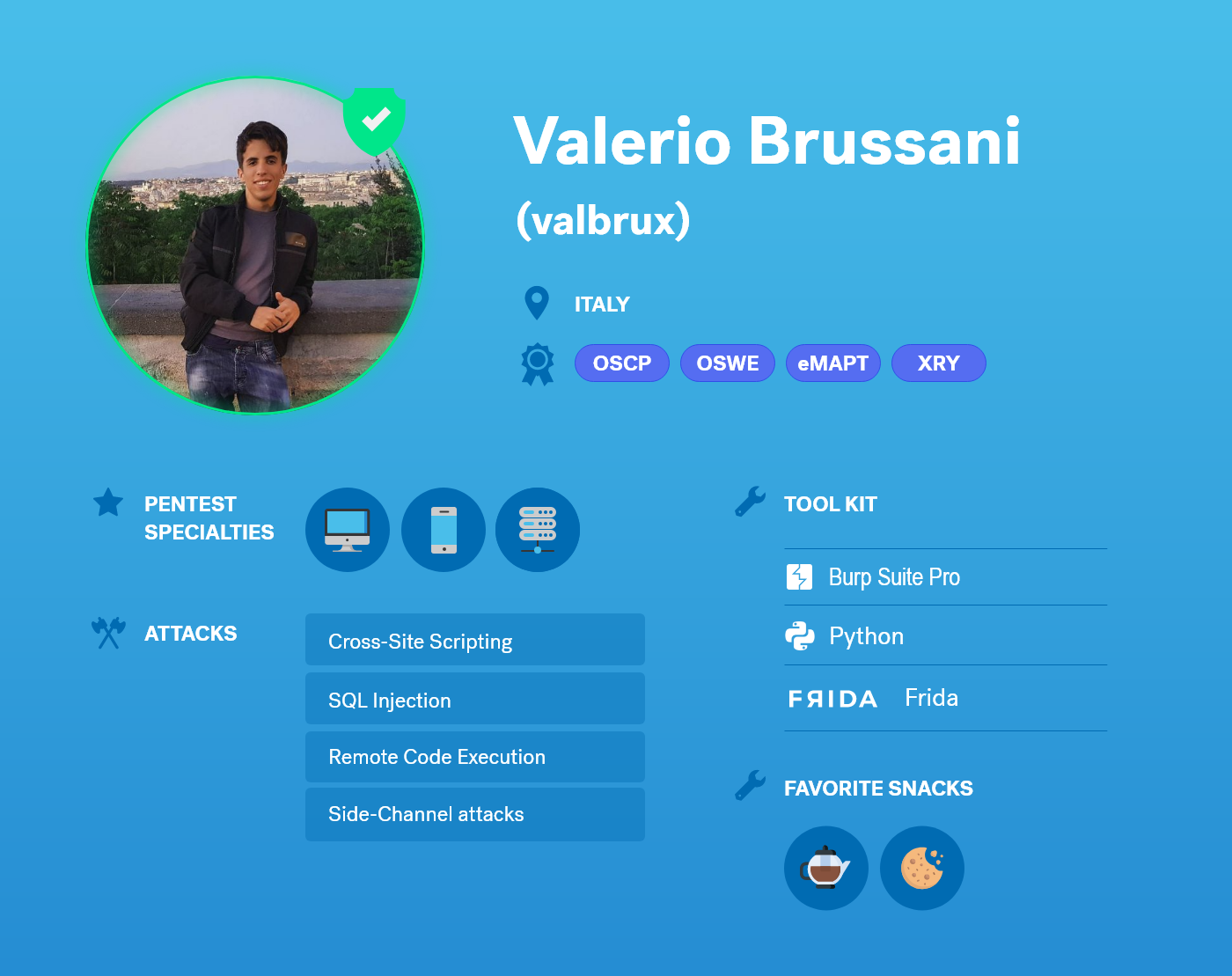
Valerio Brussani joined the Cobalt Core, our highly-experienced, geographically-diverse community of pentesters, in 2019. He is one of the 250+ pentester worldwide who has helped Cobalt secure over 2000 assets.
We had a chance to hear from him to learn more about his pentester origin story and what he enjoys about being a part of Cobalt’s pentest community.How did you get into security?
VB: I began my career on the software development side after receiving my bachelors degree in Computer Engineering. Most of my experience came from developing web and mobile applications. After some time, I decided to shift my attention more towards cybersecurity—a topic that always interested me.
This transition towards a focus in security—specifically ethical hacking and pentesting—became both exciting and challenging because it allowed me to flex my problem-solving capabilities. I’ve always enjoyed solving challenging puzzles, and I believe finding a bug is similar to this. It gives you another way to escalate your logical thinking skills. Building upon this passion and expanding my knowledge, I completed an MSc degree in Computer Science with an emphasis in cybersecurity last year.
Recently, I made the switch to full-time freelancing, splitting my time between pentesting on platforms like Cobalt as well as bug bounty platforms. I really enjoy the freedom that freelancing offers. The ability to work from anywhere in the world and plan activities around my schedule gives me a lot of versatility in my daily structure.
What motivates you when it comes to pentesting?
VB: I really enjoy the challenge of thinking outside of the box every day. This makes the work fun and it feels more like a hobby than an actual job. As mentioned above, the transition into becoming a full-time freelance pentester has also allowed me the flexibility and freedom to choose my own schedule, which fuels my motivation and keeps things interesting as opposed to a fixed schedule workplace.
What does a good pentest engagement look like?
VB: The key to a good pentest is maintaining good collaboration, where there is proper communication between pentesters and the customer. This allows for everyone involved to have a clear understanding of goals and objectives during a test.
What are the top traits that a pentester should possess to be successful on Cobalt?
VB: Curiosity: Without having curiosity, you will not have the urge to learn new things, and this is important because the world of pentesting (and information security as a whole) is constantly evolving and it’s important to stay engaged. Natural curiosity helps fuel the pentesting passion.
Technical knowledge: Each pentest requires a different approach. Having a strong technical knowledge base to build off of gives you an opportunity to learn new things, cultivates a willingness to learn, and allows you to adapt to the pentest. In addition, it helps you find more interesting and impactful vulnerabilities.
Creativity: This returns back to thinking outside-of-the-box, being able to take that curiosity and apply an element of creativity to achieve your goals. This should not be limited to just your job, but to your life outside of security as well.
Each one of these traits are not independent of one another, but rather, interconnected. Feeding a curious mind helps build your technical knowledge base, and with these skills, allows you to think more creatively during a pentest.
How do you organize yourself during a pentest? How do you manage your time and avoid burnout?
VB: With every pentest, I try to closely follow the coverage section in order to ensure that I touch upon everything during my allotted time frame. From day one of a pentest engagement with a customer I plan out my schedule in advance, allowing me enough time to thoroughly check each section during my testing process.
Due to the current situation, I’m staying quite busy. If I’m not pentesting, I am working on bug hunting in some capacity. During the summer months, I would like to take advantage of the warmer weather with some vacation breaks, but for now, I am enjoying the amount of work I have on my plate.
What kind of targets excite you the most? Do you have a favorite vulnerability type?
VB: Web and mobile are my favorite targets. There are not as many testers focusing on mobile which often means you can find a lot of cool bugs. In addition, mobile security is a rapidly changing topic and the mobile attack surfaces are less explored, which leads to newer kinds of vulnerabilities discovered daily.
My favorite vulnerability to exploit would be XSS (Cross-site scripting). In certain situations, it can be common to find; however, it can be hard to exploit because there are many protections involved, such as client-side protections or web application firewalls.
How do you learn about different security concepts? Where do you go?
VB: The first key resource for me would have to be Twitter. Whether I’m looking for new information about a specific vulnerability topic or the latest pentesting trends, it is a great place to find a wide range of security information.
I also use an app called Feedly, which allows me to compile and modify my own RSS feed. I have been using the app for almost three years and have aggregated almost 500 news sources. When I am interested in learning more about a newly discovered vulnerability, I will visit the original source to read up on how it was first discovered. If I’m looking to do a deep dive into a vulnerability, such as a scenario walkthrough, I’ll research additional resources published around that topic and basically read everything I can find on it.
Do you leverage any tools? What are your go-to tools?
VB: For web app testing, like most pentesters, Burp Suite is my number one tool. I also like to leverage different extensions, such as Param Miner and Burp Bounty Pro. In addition, I have made some custom scripts, which can be used to exploit specific vulnerabilities, such as a tool to exploit GraphQL injection flaws.
When it comes to conducting mobile app pentests, I like to use tools like Drozer and Frida.
What do you enjoy the most about being a part of the Cobalt Core?
VB: I really like being a part of the Cobalt Core because everyone is kind and collaborative, which just makes working together easy and fun. Working freelance for Cobalt also gives me the freedom to choose my pentesting schedule.
The different types of pentests that are offered on the Cobalt Platform is another great aspect. With this wide variety of applications, you get the chance to try different exploitation techniques and continually learn about new vulnerability scenarios.
What advice would you offer to someone who is interested in getting into pentesting?
VB: My first piece of advice would be to let curiosity continuously flow and try to learn something new every day. Sometimes, it may take 12 hours to learn something new, so it’s important to have that patience and passion in order to carry you through. For instance, if you are trying to find a particular bug during a pentest, this passion for constantly learning about new tools and resources helps fuel your ability to chain different vulnerabilities to achieve a higher impact for a specific flaw.
Also, having knowledge of different programming languages is important when working in security—everything is connected and understanding how things are built helps you better understand how they can be broken.
What do you wish every company/customer knew before starting a pentest?
VB: The first is to have a clear scope, which means you, as a customer, should have a good understanding of what you want to test and what you don’t want to test. In the past, I have seen this happen, a pentester tests something that the customer did not want tested, but it was not communicated ahead of time. In the end, neither side is happy, the pentester wasted their time on something that the customer didn’t want. Remember communication is key!
Something that can also be extremely beneficial for a pentest engagement is having a skilled blue team or blue teamer involved during the test. It can be difficult to communicate technical details to people if they do not fully grasp security. When you have a skilled blue team or blue teamer that is able to react and remediate, it can go a long way in achieving an effective pentest outcome.
What do you like to do outside of hacking?
VB: Lately, I have been staying active playing padel, and in the past I did a lot of swimming. It’s important to get off the screen from time-to-time, I use these activities as a way to take a break and reset.
What are your short term and long term personal or career goals?
VB: I have never spoken at a big security conference before, so I would like to get a chance to present the research I did for my dissertation on ‘Side-Channel Vulnerabilities on Android codebase.’ And of course, I would also like to continue to learn and keep finding new and interesting vulnerabilities.